I recently had to undertake some work to enable users to seamlessly authenticate to Google Apps using an identity stored in a custom Secure Token Service such as the excellent IdentityServer open source STS by Dominick Baier. The work involved is mostly configuration in Google Apps and ADFS but there are quite a number of steps and as it was non-trivial I thought I’d document it here for reference. Note that Google Apps uses SAML 2.0 tokens and because ADFS is brokering the authentication, you shouldn’t have any problems with compatibility as ADFS 2.0 can issue SAML 2.0 tokens.
Here’s a quick architecture diagram:
Key:
Green arrows = user request flow
Blue arrows = service response flow
Overview
For those of you impatient, here’s a quick overview of the steps required:
- Enable SSO in Google Apps
- Enter correct ADFS urls into Google Apps
- Upload ADFS Token Signing Certificate so Google Apps can verify the SAML tokens
- Add Google Apps as a Relying Party in ADFS
- Test
I will now walk through each stage in detail, for those who like the details.
Enable SSO in Google Apps
The first stage is to enable Single Sign-on in Google Apps. Log in to your administration console at /">http://www.google.com/a/<your-domain>/. Click on Advanced Tools and in the Authentication section click on Set up single sign-on (SSO):
This will take you through to a configuration screen. Make sure the checkbox next to Enable Single Sign-on is ticked, and then enter the following values:
Sign-in page URL: https://adfs.yourdomain.com/adfs/ls/
Sign-out page URL: https://adfs.yourdomain.com/adfs/ls/
Change password URL: https://sts.yourdomain.com/startersts/users/password.aspx
Verification certificate: Upload the ADFS Token Signing cert (.cer file) which you can obtain from the AD FS 2.0 Management Console (under Service > Certificates). Remember to click Upload.
Check the box next to “Use a domain specific issuer”.
Enter some network addresses into the Network masks box if you wish.
At this point Single sign-on is configured and enabled. Note that this will take immediate effect on your access to Google Apps services so beware! However it does not affect your login to the admin console – that is always accessed via a manual login, so you can get in and turn it off again.
Configure ADFS
Open up the AD FS 2.0 Management Console and navigate to the Relying Parties section. Click Add Relying Party Trust and follow these steps:
Choose Enter data about the relying party manually
Provide a name for the trust (not important, only so you can easily identify it)
Choose AD FS 2.0 profile
Tick Enable support for the SAML 2.0 WebSSO protocol and enter /acs">https://www.google.com/a/<your-domain>/acs into the Relying party SAML 2.0 SSO service URL
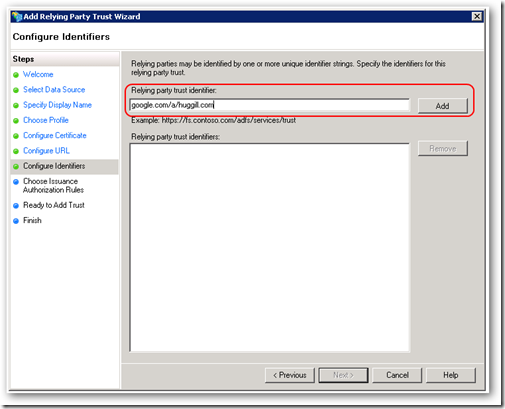
Enter google.com/a/<your-domain> as the relying party identifier
Complete the wizard.
Then click on the newly added item and click Properties. Click on the Signature tab and click add:
Here we add the Token Signing Certificate – it must be the same one that we uploaded in the Google admin console, and this should be the ADFS Token Signing Certificate.
Once you’ve done that click OK to close the Properties dialog.
Now click Edit Claim Rules and click Add Rule:
Select Transform an Incoming Claim from the Claim rule template drop-down:
Give the rule a name, select E-Mail Address as the Incoming Claim Type, set the Outgoing claim type to Name ID and the Outgoing name ID format to Email:
Finish the wizard.
Test
I’ve assumed here that you’ve already got your custom STS configured as a Claims Provider in ADFS. To test the end-to-end service, visit http://mail.google.com/a/<your-domain>. You should get redirected to ADFS. Choose your STS and then enter your credentials. You should then be redirected back to Google Apps and arrive at your mailbox, logged in.
If you hit problems, check these items:
– You’ve got the correct certificate uploaded to Google Apps and configured in ADFS
– The time on the ADFS server and custom STS servers is correct
– Google Apps SSO configuration is correct
– If all else fails, try Googling!












Man, that was exactly what i was looking for. I will try to implement it tomorrow.
Best regards.
Great, glad it helped – let me know how you got on
I would like to configure ADFS for three different partners is it possible?
We have created one Instance on GoogelApps with Google Sites ,Gmail and Google Drive which will be shared by all three companies
All three companies are different using their own AD .There is no plan to create trust/federation between these three AD domains. User from respective company should be able to access Google Apps using their own AD Credentials.
Please advice
Hi Shuggil,
I followed your article . Im getting error “this account cannot be accessed because we could not parse the login request”
We enabled RelayState on our ADFS . we are using ADFS 3.0.
Any thoughts
Great post with clear steps. I found that when initiating a SSO call from ADFS to google apps you have to set an outgoing claim rule from ADFS to Google with an ADS attribute store. One question, how did you solve the sign off redirect issue from Google Apps back to ADFS?
Hi Scott,
Google Apps expects a Name ID formatted claim, so you do need some claim transformation rule to convert whatever incoming claims you have (in my example an email claim, but from AD it could be the UPN or account email) to the required outgoing claims.
I haven’t solved the single-sign out issue yet – all I can see is that I get an ADFS error when trying. If you make any progress I’d certainly be interested.
Hi, we used your blog to get Single Sign on working and it helped immensely, so first I just want to say thank You.
I was wondering if you were ever able to get the Single sign out to work correctly?
Thanks Glen, glad it was helpful.
I have not done any further work on Single Sign Out yet – but watch this space!
I’m sure I just don’t understand ADFS well enough, or maybe I’m not understanding what you’re trying to do, but why do you need the custom STS? Isn’t ADFS an STS?
Yes, ADFS can provide authentication using it’s built in Active Directory claims provider trust. However, in my situation the user credentials are stored in a custom database (happens to be MS SQL Server but could be anything) and therefore I use a custom STS to provide authentication. If you only need Windows Authentication (i.e. because your clients are logged on to a Windows domain that your ADFS server has access to) then all you need is ADFS.
In regards to the token signing certificate. Will the auto-generated one, which is my internal FQDN, work? Or will I have to issue a new cert with the servers external FQDN?
The auto-generated ADFS token signing certificate will do fine, in fact I’m using the auto-generated one. I haven’t seen any performance issues with using a non-publicly issued cert for this.
Hi,
I have a one big problem that is, Could you help me to complete “post development configuration for ADFS” in Windows server 2012R2 Standard. I’m getting problem to get SSL certificate to complete ADFS configuration. How I will create appropriate SSL certificate to complete this ADFS configuration, If you help me with details then it will be very helpful for me. Looking for your reply.
Best Regards
Thanks a lot for the article post.Really looking forward to read more. Really Cool.
Thanks for the info on the cert. Apparently my problem is that the NameID Element is missing from my SAML Response. Thought I followed your directions to the letter, but I may be missing something.
Following your directions for the claim rule NameID is never set in the SAML Response. If I create a claim rule using LDAP attributes I can get it working, but that is gonna make things difficult for me. Got any suggestions?
Hi Jason,
Have you tried different types of claim type in ADFS? I suggest playing around with the format field too. Then if you can run a HTTP inspector like Fiddler, you can check the SAML response from ADFS yourself.
HTH,
Sam
I make everthing okey.
my domain is istanbulticaret.edu.tr but my google domain is icu.edu.tr I am not using STS only active directory authentication. what shoul I have to make on transform rule.
google redirect to my server I enter usernmae and password but do not accept the password.
thanks
Hello. Thanks for the step by step information. We have a windows 2003 environment on campus. We are in the process of provisioning and setting up Google Apps for our students using Single Sign On option for authentication and are looking to use ADFS 2.0 on a Windows 2008 R2 server. Can ADFS 2.0 co-exist in a 2003 environment? If so, does authentication really work in the 2003 environment using ADFS 2.0 or do you need at least one 2008 domain controller in mixed mode and another ADFDS server as well?
Hi Vinny,
I’ve not had any experience mixing environments however I would imagine that you could easily add the Windows 2008 R2 server to the 2003 domain and run ADFS 2.0 on it. I don’t think there is anything special about the AD requirements.
I’d be interested to know how you get on, do post back.
We had used these steps to setup our Google SSO solution over a year ago, and it broke the other day. Part of the issue was due to certificate expiration. The other part had to do with the fact that the SAML response no longer contained the NameID element.
We had to create an “Send LDAP Attribute as Claims” rule that extracted the “E-Mail-Addresses” as “E-Mail Address” claims, and further had to create a transform rule to take that claim and output it as a NameID element with the EMail format.
I had to modify the transform rule because the “format” attribute of the NameID element in the output did not match what Google was looking for. Namely, ADFS was outputting “urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress” when Google expected “urn:oasis:names:tc:SAML:2.0:nameid-format:email”. What’s confusing about this in particular is that it is an ADFS 2.0 server and the RP is a SAML 2.0 profile, so why would this output a 1.1 format identifier?
Hmm interesting. Sounds like I should revisit this in light of some changes at Google. Vis the versioning, this might be a confusion between the SAML protocol and the SAML token format.
@Jason
How do you create a claim rule using LDAP attributes? I am having the same problem with no NameID being set in the SAML Response.
That’s ok. I figured that out using the following link:
http://www.john-james-andersen.com/blog/service-now/ad-fs-2-0-working-with-servicenow-saml-2-0.html
See section:
AD FS Relying Party Claim Rules
Thanks for a very helpful post. You’ve explained almost everything. Is there any chance you could explain more? I’m trying to configure Google Apps SSO to work with ADFS on Active Directory. The part I don’t understand is “I’ve assumed here that you’ve already got your custom STS configured as a Claims Provider in ADFS” I not using a custom STS. I just want to use ADFS and Active Directory. I’ve found nothing on the internet nor Google Apps help to configure this part. Could you explain or point me to a resource?
Hi Dennis,
If you are using Active Directory then it is very simple – all you need to do is make sure that your ADFS server (if it’s a different machine to your Active Directory domain server) is joined to the Active Directory domain that you wish to use. ADFS comes with a built in AD claims provider for the domain that it is part of. No further config required.
Hi, I was wondering how this would affect users who add their gmail to their mobile devices. Would that still work? since Google potentially no longer has their updated passwords.
As far as I can see iPhone access is authenticated directly with Google, rather than through ADFS (see http://harwoodhill.com/blog/2011/05/iphone-password-error-with-google-apps-sso/). Therefore I think you would need to set up some sort of password sync between the two.
Hi shuggill,
I have got few enquires in providing SSO access to google apps. Can u give me your email id so that I can email you.
Thanks
Prasanna
Yes it’s sam [at] huggill [dot] com
This should solve the sign out problem for Google Apps and ADFS 2.0
http://social.msdn.microsoft.com/Forums/en-US/Geneva/thread/bcab09d1-9f33-4ef9-a54d-dbeace628771
Hi Shuggill,
I have configured SSO using ADFS for Google Apps.When we tried testing the configuration by entering the url http://mail.google.com/a/ it gets redirected to ADFS but at this point I get a google server error.
Is this error because the domain created by me is not registered on the internet and is a local domain for testing purpose only.Do I need to buy a public ip and domain for successful redirection ?
Thanks and Regards,
Anita
What is the domain you are usng?
Sweet blog! I found it while surfing around on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there! Cheers
Hi Shuggill,
I have tried to configure SSO for Google Apps using ADFS but I’m getting the following error:
“Server Error: We are unable to process your request at this time, please try again later.”
This is what I have done:
1. I have an AD (it’s on a virtual machine) — NOT on public network
2. I configured an ADFS on that server
3.I enabled SSO for Google Apps
4.I added a Relying Party Trust in ADFS
5.I tried to open Gmail service for my domain
6.I am getting redirected to ADFS
After I enter the username and password , the error message appears:
“Server Error: We are unable to process your request at this time, please try again later.”
Do I need to make any DNS entry for my DC ? I followed your blog but I was not able to successfully configure it.Can you please help..
Regards,
Samvit
When you get the error message what is the URL in the browser? Is it ADFS or Google? If it’s ADFS, you can open the Event Viewer on the ADFS server, then expand Custom Logs and the ADFS node to see ADFS related events, that should show you some further details on the error.
Hi Samvit,
Where you able to resolve this issue. My setup is similar as yours. Appreciate any help provided.
Regards,
Dinesh
Hi Shuggill,
Thanks for the step by step information!
I’m getting a Google Server error after having configured ADFS 2.0 using the steps you provided. When I investigated the HTTP headers, I found that the decoded SAML response contains an “EncryptedAssertion” block instead of an “Assertion” block. How do I change this encrytion setting in ADFS? Also, since I am using AD as an Identity Server do I need to make any changes in the “Transform Claim Rule” wizard to convert incoming claims to UPN or account email instead of an email claim like you mentioned in the second comment above.
Awaiting a quick relpy.
Thanks! 🙂
Hi,
ADFS will be encrypting the response IF you have set an encryption certificate up on the ADFS configuration for the relying party. To check / change this, open the ADFS configuration application, click on the Relying Party Trusts item on the left hand tree, and double click on the relevant item on the right (the Google Apps entry). Click on the Encryption tab and remove any certificates there.
Once you’ve saved the changes try again, and you should see that ADFS is no longer encrypting the contents of the token.
Great article – being able to provide SSO to Google Apps from Active Directory (or ADFS) will help with a solution that I am proposing where by users in the organisation from across the globe need to collaborate and given the current IT environment of this organisation – Google Docs is perhaps a better bet than trying to implement any type of collaboration or content management solution
Hello,
Do you know if it’s possible to add multiple idp for the Google Apps? For instance, would it be possible to use another SSO for the Google Sites than the one I use for GMail ? THanks!
Hi,
Great article SAM. Very insightful indeed.
But I would be very grateful if you could shed some light on the problem I have.
I have a web-application, which is using 2-Factor Authentication, the 1st one being AD username & Password. Now this web-app is internet hosted and doesn’t reside on any internal domain. It connects to an AD domain via LDAP.
In this same application, we want users to be able to send & receive their Gmail emails but with SSO. We don’t want them to re-enter a username & password for their gmail account. Instead, the user’s can store their Gmail username in a User attribute(like Description) in Active Directory.
Both the Identity Server and our web-app will be on same internet hosted server but will not be part of any AD domain as both our web-app and Identity Server will be used for multiple domains.
Identity Server should be able to receive Domain Details and Service Account details for a particular domain from our web-app.
When user logs into our web-app, an automatic SSO request for Google goes to the Identity Server with info for the domain, the user belongs to. SSO request gets filled and a session is built. Then user should be able to see Gmail Emails, Contacts, Calendar, etc. in our web-app only.
I don’t know if this is possible at all.
Any suggestions for this or do achieve similar functionality will be much appreciated.
Hi, has anybody actually managed to get SSO working with ADFS 2.0 and Google Apps?
Though your instructions for ADFS are sound to a point shuggill, it still leaves us wondering “Whate are we missing?”.
When we are testing we are getting a web site error with a code that changes frequesntly. From the Internet we can get to our web server via port 80 and we see the default web site. However, using port 443 (which is open) we get:
There was a problem accessing the site. Try to browse to the site again.
If the problem persists, contact the administrator of this site and provide the reference number to identify the problem.
Reference number: 961fd754-c951-464b-a50e-453f1ccbe5b0
Internally we browse to the server /adfs and get: HTTP Error 403.14 – Forbidden
We browse to /adfs/ls and get the error above also
Google SSO just fails so tracking back as you suggested.
Is this an IIS issue? We have trawled Google/Microsoft but to no avail other to look at SSO Easy who want US$2500 for a handful of users.
So far, no-body has published results on how to get this working as if it is some black art or something.
Would appreciate any feedback.
I have tried as you configured for Google Apps S SO. I am using Active directory as authentication store. After hitting the mail.google.com/a/domainname url its redirect to my ADFS , after entering the credentials Google Apps throws “This account cannot be accessed because we could not parse the login request”.
I have used same configuration as you mentioned in articles.
Doubts that I have
Shall we need both AD and Google Apps domain to be same. In my case i have username@abcd.com as AD domain and username@efgh.com as Apps domain. I have added UPN suffix as efgh.com in Active Directory.
Help to resolve the issue
Hi,
Thanks for your step-by-step document. It is very nice.
I am new System Admin, I am following your procedure and I have some doubts,
1) Our website is like example.com hosted with external, but our AD domain name is like example.local, is it workout?
2) For redirection, do I need to buy a public IP? or LAN IP is enough?
Thanks again,
Perumal
Hi,
One more question, whether the Single Sign-On (SSO) will work on Google Apps – Free Subscription?
Hello Sam,
First, congratulations for your help.
I did as your procedure, and this redirect for authentication, however when I put User and password, ask again (as if you were wrong).
Have you any idea what can be?
Thanks in advance
Hi Rafael, I know this is an old post, but to help anyone else who may have the same issue.. if it keeps asking for reauthentication, its because you are using a self signed certificate and you havent added it to your trust root certificate store on your local computer.
I’m running into that exact same problem. If I input a bad password it tell me it’s bad. But if I input the right password the page just reloads.
Did you ever figure it out?
Hi,
I have integrated SAML2.0 to ADFS 2.0 using artifact binding for a third party client. The third party client is pointing that SubjectConfirmations were invalid because Assertion inResponseTo value is null. This is the part where this attribute value should be present . where to enable this inResponseToattribute in ADFS 2.0 ?
Part of the SAML response where it is expecting inResponseTo attribute:
ABBHAN
Thanks, Ashish
Hello All
The token-signing certificate was upgraded and a new one was generated as primary and now the login for Service-Now is not working.
We import the new token-signing certificate and set it as active but we havent had luck.
What basically occurs is that when we try to login in, it automatically logs the user out and says logout successful.
Is there any other steps that need to be performed when the self-signing certificate is updated?
Thanks
Hello shuggill,
Great post Shuggill.
There is some tricky issue which i was facing and would like to share with you, Im using SSO to authenticate my webapp and working fine with SAML and also configured a sharepoint site to use the same SSO as the identity provider..
There is two use cases 1. Access Sharepoint site -> SSO(redirects to WebApp login page and validate) -> return to portal. (Installed ADFS 2.0 and working fine)
2. Accessing WebApp with same logging page and authenticating -> from webapp page i need to go Sharepoint site(pass through with same token key though we have already authenticated) – when we are testing we are getting a web site error like ‘There was a problem accessing the site. Try to browse to the site again.’
Note: Not using Active Directory.
Would appreciate any feedback on the issue.
Awesome post.
Hi Mate,
Great write up. I was trying to get this going in ADFS 3 but, I found that following your steps with adfs 2, i got much further…
I was wondering though, did you ever come across Google’s site responding with “Google Apps – The required response parameter RelayState was missing.” ?
I believe I have even added the relay state in the web.config and ran iisreset and reset adfs service..
Pretty! This was an incredibly wonderful article. Thanks for supplying this information.
Hi Sam,
Great article, we used the same process to setup ADFS 3.0 and works well for a SP initiated and also accessing by using a relaystate URL.
Our issue is, when trying to access google apps from the drop down menu from ADFS initiated sign on page. we receive the error message “Google Apps – The required response parameter RelayState was missing”.
We added the line “” but still does not work.
Do you know if this is from a google side or Microsoft? also do you know if you can remove/hide the relying parties from the ADFS initiated sign on page?
Cheers
Collo
Hi mate,
Thanks for sharing valuable knowledge. I followed your instructions and successfully integrated google apps for education with ADFS 3.0 on Win SRV 2012 R2.
However it is true that now we need two claim rules. First we have to use “send LDAP attribute” and select
Email Address -> Email address
And then second rule is to transform an incoming claim:
Email Address -> Name ID -> Email
I hope this helps and would appreciate if you can update this thread.
Thanks agaiin.
Great article. I currently use GADS and GAPS to simply sync my AD info to Google. I’m considering this option instead. Do you know if the ADFS method works with Chromebooks? I’m not sure if it would as they require a Google ID to authenticate with. Thanks.
Hi
I completed your procedure i just have a couple of questions.
In terms of the domain if mine is ( external – example.com) (internal – example.local) How do i get google and ADFS to recognise this?
When you refer in your steps ” Enter google.com/a/ as the relying party identifier” Is this suppose to be your internal domain or external?
Do i need to configure anything else? You also stated in one of your steps about configuring an STS?
“I’ve assumed here that you’ve already got your custom STS configured as a Claims Provider in ADFS.”
Hope you can assist me
thanks
Joe
Hi,
Has anyone seen this error:
“The required response parameter RelayState was missing:
Config is- ADFS 2.0 ..trying to set up SSO to Google Apps….any direction would be great.
Hello Sam
I configured our ADFS as your steps but cannot access gmail it’s always get:
This account cannot be accessed because the login credentials could not be verified.
please help
Your article got me pretty far. For that I thank you. I now have ADFS setup and it’s working as far as I can tell. However, my situation is a little different. In my organization I have ALL Google apps turned off with the exception of Gmail which is hosted offsite so even that app wont load (and it’s not supposed to). The only Google URL that we ever visit is http://email-quarantine.google.com/messagecenter.
Here’s my deal….I previously used a PHP SAML2 idp solution. I forget where I got it. But I used it with the Google message center and it worked fine. The area where I setup SSO on Google is the same as you show here. However we are ditching PHP so I need to find something else.
With everything setup, this isn’t working and I’m not sure how to configure the Relying Party for use with Message Center because it’s a different URL. If I set it up verbatim to what you have and I login as any domain user using the wrong password my adfs page tells me the login is wrong. If I login with the correct creds the page just reloads and stays on my adfs page. It never goes to the Google Apps page which it should then tell me no apps are available. Plugging in the Message Center URL does the same thing though. My ADFS page just flickers and stays on that page. Nothing is recording in the logs unless I put in a wrong password.
Have you ever come across this issue?
Did anyone try this at 2016 after all these updates ?.
Hi Sam,
Great post – thank you!
I managed to get this working today with one adjustment, which is to add a claim rule before the claim rule the one you write about
a. Right-click on the relying party trust and select Edit Claim Rules….
b. On the Issuance Transform Rules tab select Add Rules….
c. Select Send LDAP Attribute as Claims as the claim rule template to use.
d. Give the claim the name Get LDAP Attributes
e. Set the Attribute Store to Active Directory, the LDAP Attribute to E-Mail-Addresses, and the Outgoing Claim Type to E-mail Address
f. Click Finish