My kids are BIG Minecraft fans! We've been enjoying playing Minecraft on nearly every device in our house: Minecraft for iPadMinecraft for PCXbox 360Xbox One SMinecraft Pocket Edition on iPhoneAnd now with Santa's visit...Minecraft on Nintendo Switch! That's a lot of Minecraft! I run our own Minecraft server at home so that everyone can play... Continue Reading →
Configuring SQL Server Kerberos for Double-Hop Authentication
The Requirement We have one database stored on SQL Server (A), which has some synonyms to tables in SQL Server (B). We want our .NET 4.5 application (running under IIS) to invoke some queries to move data from tables in SQL Server (A) to SQL Server (B), using the synonyms (so the web application doesn’t... Continue Reading →
Solving PPTP VPN Error 619 when behind a TMG 2010 firewall
I was recently configuring a test environment which had a Microsoft Threat Management Gateway (TMG) 2010 firewall between the private network and the Internet. From a test Windows 7 client I was trying to establish an outbound PPTP VPN - but I kept getting Error 619 "A connection to the remote computer could not be... Continue Reading →
Solving ‘An exception occurred in publishing: No such interface supported (Exception from HRESULT: 0x80004002 (E_NOINTERFACE)’ with Visual Studio 2012 RC
So I’m using Visual Studio 2010 RC and loving web deploy as a simple way to publish my projects to different environments. However a problem cropped up today after installing some web tooling updates: ‘An exception occurred in publishing: No such interface supported (Exception from HRESULT: 0x80004002 (E_NOINTERFACE)’ I couldn’t even open the publish settings... Continue Reading →
Configuring multiple public DHCP IP addresses on a Linksys WRT54G with OpenWrt
I hit a problem the other day whilst trying to map a bunch of public IP addresses (provided by Virgin Business) to various services within the network. Essentially I’m running a VMWare ESXi server with several web servers on, and I want to use the public IP addresses to expose these servers to the Internet... Continue Reading →
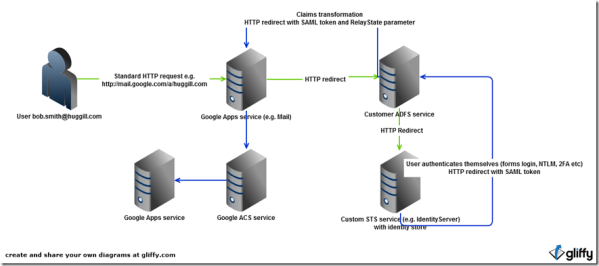
Setting up Google Apps Single Sign On (SSO) with ADFS 2.0 and a custom STS such as IdentityServer
I recently had to undertake some work to enable users to seamlessly authenticate to Google Apps using an identity stored in a custom Secure Token Service such as the excellent IdentityServer open source STS by Dominick Baier. The work involved is mostly configuration in Google Apps and ADFS but there are quite a number of... Continue Reading →
Clearing up the confusion over session timeouts in PHP and Zend Framework
I’ve recently made a foray into the world of Zend Framework. If you’ve not come across it, it is one of several popular PHP frameworks that implements the Model View Controller software architecture. By day I’m mostly devoted to hacking ASP.NET MVC, but having had some experience with PHP I decided to get my teeth... Continue Reading →
Using O2 ZTE MF100 Mobile Broadband on Mac OS X Lion
A few days ago I took the leap and upgraded my Macbook Air to OS X Lion. After a seamless (and typically Apple) upgrade process, I was enjoying the benefits of an even more refined operating system. However, one of the first things I did was test out my mobile broadband - and there the... Continue Reading →
Building a budget VMWare ESXi server
The Background One of the projects that I've been working on recently requires a lot of interaction between different systems, and in order to roll-out changes and carry out integration testing I needed a replica of our production environment. However the challenge was that it required 7 machines to replicate production. In the past I've... Continue Reading →
Synchronising Highrise, Basecamp and Google Shared Contacts–Part 2
Background: In Part 1 of this series I wrote about a recent project that I worked on to synchronise contact data between a number of web applications, and how I had to work around the (current) shortcomings of their APIs. As Scott Hanselman says, “talk is cheap – show me the code”. So here we... Continue Reading →